중국산 Vidmate 라는 앱이
개인정보 유출, 배터리 광탈, 유료 사이트에 몰래 강제 가입
등의 사악한 짓을 한다고 합니다.
Popular Android App VidMate Is Charging People, Draining Their Batteries, And Exposing Data Without Their Knowledge
↻
http://www.buzzfeednews.com/article/craigsilverman/vidmate-app-download
Posted on May 19, 2019

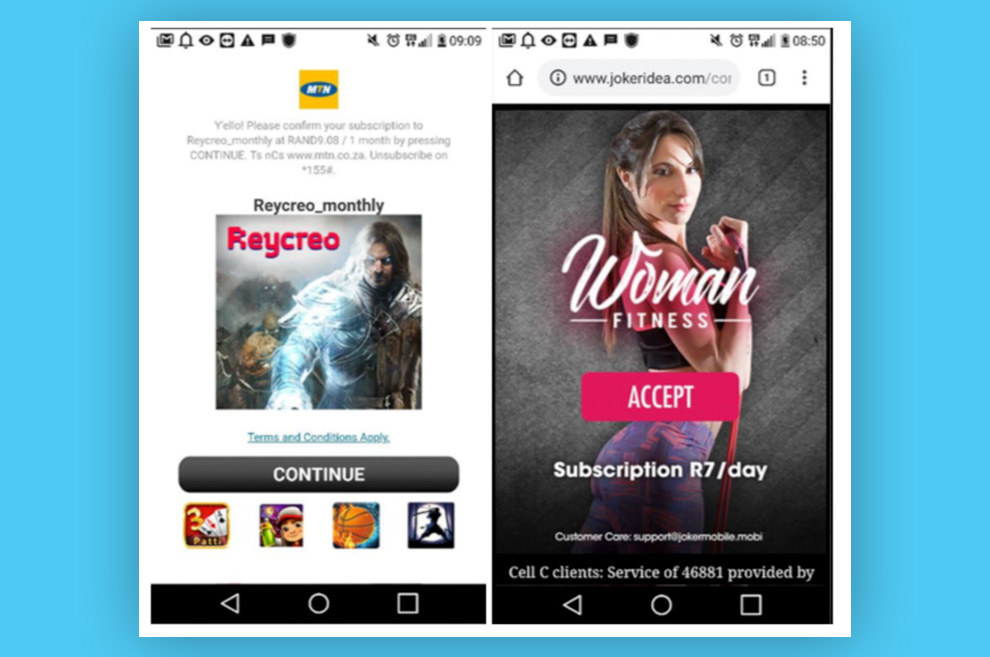
More than half a billion people have installed VidMate, an Android app that enables them to download videos from YouTube, WhatsApp, and other plats. This functionality made VidMate, which has ties to Chinese tech giant Alibaba, hugely popular in countries such as India where streaming mobile video can be expensive or at times unreliable.
But it appears that convenience still comes at a high cost for users. VidMate has been displaying hidden ads, secretly subscribing people to paid services, and draining users’ mobile data, according to findings from security researchers at a London-based mobile technology firm.
Researchers at Upstream say VidMate subjects its users to a range of suspicious behavior that could be costing them money, draining their phone batteries, and exposing their personal ination.
During a Skype interview, a VidMate spokesperson denied that the app knowingly engages in suspicious activity, and said it is investigating. He also declined to provide basic ination such as the names of VidMate executives and funders, and did not respond to follow-up questions, including a request to confirm his name and title.
Guy Krief, the CEO of Upstream, said users who download and open VidMate “surrender control of their phone and personal ination to a third party."
"The phone and its connection become part of a botnet and are used to commit ad fraud, at the expense of its owner ... and his privacy,” he said. (The alleged ad fraud occurs in VidMate when it displays ads that users can’t actually see.)
Over the past six months Upstream blocked more than 128 million “suspicious” transactions by the VidMate app that could have cost users in Egypt, Brazil, Myanmar, and elsewhere more than $150 million in unwanted, unauthorized mobile subscriptions, according to the company. Upstream said it began blocking these transactions as early as 2017 and saw their volume dramatically increase late last year. VidMate was developed and owned by UCWeb, a subsidiary of Alibaba, prior to being sold off last year.
A VidMate spokesperson who used the name Jiatao Chen on Skype told BuzzFeed News it takes the findings by Upstream seriously and blamed any alleged suspicious behavior on third-party software development kits (SDKs) and partners.
“No only do we not program such practices into our core app, we have a zero-tolerance policy because it is in VidMate’s interest to protect our users against such detrimental practices,” he said.
Chen said VidMate already terminated its relationship with one partner implicated in the Upstream report, and continues to investigate.
UCWeb and VidMate both told BuzzFeed News the app and its trademarks were sold to a new entity, Guangzhou Nemo Fish Technology Co., in 2018. They said the companies maintain a business relationship but are separate.
“Since our divestment early last year, we’ve maintained a business collaboration with Vidmate, just as we have with other apps that we are working with. We are not involved in any of Vidmate’s operations,” said an emailed statement from a UCWeb spokesperson.
Chen described Nemo Fish as a startup but declined to name its executives or shareholders during an interview, and did not respond to follow-up questions. A second VidMate spokesperson later contacted Buzzfeed News by email to repeat much of what Chen said, while also questioning Upstream’s methodology and findings.
That VidMate spokesperson’s email account used the name Alice Granger, which is also the username of a Twitter account that sent thousands of spam replies to people in 2015 suggesting they download VidMate. Granger did not reply to follow-up questions about the Twitter account, or ones that asked for the names of Nemo Fish/VidMate executives and funders.
Though it’s unclear exactly who owns and operates VidMate now, Krief said his company began blocking suspicious transactions from VidMate long before UCWeb sold the app.
“We saw some first small volumes of suspicious transaction requests in October 2017 and it progressively ramped up until April 2018 when it then started being at a different scale,” he said.
The UCWeb spokesperson said in an emailed statement that the company can’t respond without seeing more details and data.
“To date, Upstream has not contacted us or supplied us with the ination upon which they are making their claims. On that basis, it is impossible for us to evaluate their assumptions,” the statement said. “Overall, UC always seeks to provide a safe, secure and enjoyable user experience and has stringent rules and regulations in place to ensure that is the case.”
These findings are yet another example of a Chinese app allegedly committing ad fraud and abusing user permissions and data at a global scale. BuzzFeed News has previously revealed ad fraud and other malicious behavior in apps from major Chinese developers Cheetah Mobile, DO Global, and Kika Tech. As a result of an investigation published last month, Google banned DO Global from the Play store and its advertising products. DO is partly owned by Baidu, one of the largest tech companies in China.
In January, Upstream also revealed that a hugely popular weather app from TCL, a Chinese handset and app company, was fraudulently subscribing users to paid services and collecting suspicious levels of personal data. The app was removed from the Google Play store as a result of Upstream’s findings. (VidMate is not in the Play store but is widely available from other Android app stores.)
Krief says the Android ecosystem combines with digital advertising to create a huge opportunity for fraudsters.
"Android’s open nature allows for the wide distribution of mobile malware. And digital advertising's complexity empowers fraudsters — it is a worldwide playground with low risks and high incentives," he said.
Examples of hidden ads identified by Upstream.
Upstream
Examples of hidden ads identified by Upstream.
Upstream identified the issues with VidMate in the course of providing security services to mobile carriers in 18 countries, primarily in the developing world. The company monitors activity on the carriers’ networks for ad fraud, malware, and other vulnerabilities, and conducts investigations when it spots a pattern of activity.
VidMate “was number one in terms of block attempts over the past six months” among all the apps on the networks Upstream monitors, Krief said.
The security company also received complaints from users who said their phones were behaving strangely and at times adding paid subscriptions without their knowledge. Upstream acquired and monitored three phones that had VidMate installed. It soon detected VidMate surreptitiously downloading and installing a software development kit from an entity called Mango that loaded hidden ads and secretly signed up users to paid services.
The suspicious activity often took place while the phone’s screen was locked and not in use, according to Krief.
Both VidMate spokespeople said the Mango SDK is made by a Chinese company that partnered with VidMate. Neither responded to a request for the name and contact ination of the company.
“Our tech team is already pering in-depth analysis on this SDK, if this SDK really is pering ad fraud, Vidmate will terminate relationship with and blacklist this company,” the Granger email account said in its message.
Upstream claims that the unauthorized activity in VidMate ate up huge amounts of mobile data — more than 3 gigabytes per month, which Upstream estimates could cost $100 a year, or half a month’s wages in markets such as Brazil.
VidMate also collected personal ination without notifying the user. This data, which included a unique number associated with a person’s phone and their IP address, was sent to servers in Singapore belonging to Nonolive, a streaming plat for gamers that is funded by Alibaba.
Chen, the VidMate spokesperson, told BuzzFeed News it terminated its relationship with Nonolive after learning of the “abuse of user ination.”